I'm fascinated by how cybersecurity enthusiasts and organisers present and run their events, as that seems to be crucial in (a) getting people to come along, (b) triggering action.
I attended three cybersecurity events in September – Cryptoparty London, Cy3sec and Cybersecurity for 'Real People' – and learnt a lot from how they engage, or don't. Conclusion: Infosec events need to be a LOT more practical and engaging and to deliver on what they promise. Drinks/snacks also help with after-work events.
1. Cryptoparty London

Organised by:
A tech consultancy and a civil rights group put together the London event but this is just part of a larger decentralized movement of CryptoParties with events happening all over the world. "The goal is to pass on knowledge about protecting yourself in the digital space. This can include encrypted communication, preventing being tracked while browsing the web, and general security advice regarding computers and smartphones."
https://www.cryptoparty.in/london
Approach
Put it in a bar, call it a 'party', have infosec-themed cocktails, offer interactive break-out workshops (on Tor browser, Bitcoin, email encryption and smartphone surveillance) and lightning talks with a stage and large screen, surveillance-based visuals, digital art and music. September was the tester – it went very well and is now going monthly.
Pros
- Beginners welcome
- Networking, sense of community, expert access
- Top pedigree of speakers, eg, Silkie Carlo, co-author of Information Security for Journalists
- A nice dark room and sociable vibe for tired people after work
- Practical workshops, how-tos and Q&As
- Stickers and swag on the tables
Cons
- It's held in London – I'm in Birmingham
- It ran way over time so I missed my second workshop
- Logistics – bar noise/numbers made workshops hard to hear for some
- Attendees seemed highly engaged and knowledgable already – bar too high for newbies?
Summary
CryptoParty's main objective is to "tear down the mental walls which prohibit people to even think about these topics" – on that aim, it was definitely the best for engagement and practical learning. I'm now set up on Tor Browser and just wish I could have stayed longer.
2. Cy3Sec
Organised by:
Fizzpop – a popular Birmingham-based maker/hacker group with its own workshop space. Its first cybersecurity workshop was set up on Meetup and is set to run monthly.
https://www.meetup.com/fizzPOP-Birminghams-Makerspace/events/243198601/
Approach
One presenter talking to attendees around a table, small group style. There was a tech fail on the projector front which didn't help. The speaker was a real-life locksmith so the focus was very much on how the hackers break in. The Meetup blurb said:
"The first hour will be on 'beginner' topics, then half an hour to chat, then an hour on a more advanced topic(s). If people want to do a short talk, great. There may be Bluetooth lock picking. There might be hacking a local server. A talk on decapping chips. If you've something to teach or explain about, please let us know."
Pros
- Beginners welcome
- Quiet workspace, easy to get involved
- Unusual angle – locksmith/hacker, physical access to devices
- Free-roam topics and tech nerd view (how to kill people and start wars through hacking) = an interesting experience!
Cons
- Attendees were Fizzpop members, a brain surgeon and a someone with a Masters in cybersecurity – not exactly beginners friendly
- Mostly a one-way talk, lots of assumed knowledge, and attack based with cybersecurity solution more an afterthought
- Departed from promised structure and timings
- Sense of being an outsider entering a tech nerd's member's club
Summary
I never knew where this session was going or what I was going to get or even when it was going to end. Some structure and communication would really help this session. The Fizzpop-style focus on physical hacking and USB baiting, and 'how stuff works' was way above my knowledge grade but learning how to hack could fill a useful gap if done at beginners level and with a sense of playful fun that is the Fizzpop way.
Despite the exclusive feel, I am tempted to go back – albeit with a flask of tea and some biscuits, and just enjoy the random weirdness of Fizzpop life.
3. Cybersecurity for 'real people'
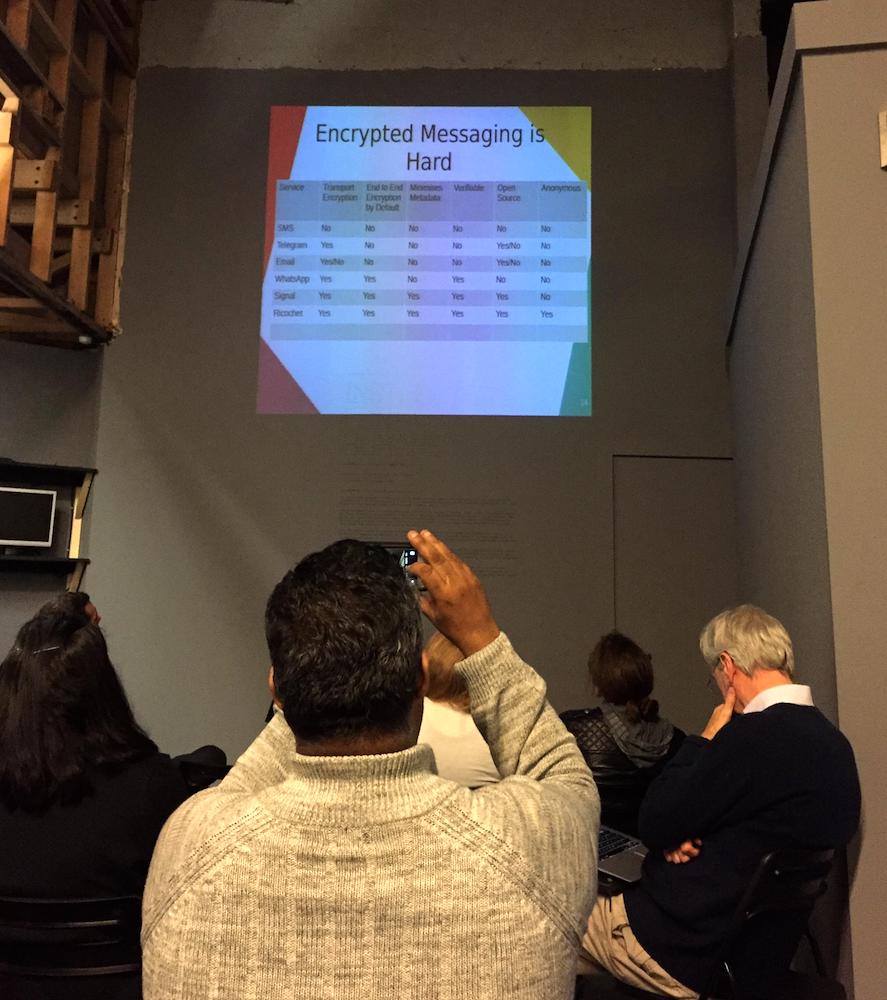 Organised by:
Organised by:
The Open Rights Group Birmingham – which runs regular events on cybersecurity and data privacy for concerned citizens. It feels more political although the offer is also practical. It campaigns to protect and promote digital rights in Birmingham and beyond. It was also set up on Meetup:
https://www.meetup.com/ORG-Birmingham/events/242706511/
Approach
The purpose was to offer practical cybersecurity advice that ‘real people’, not just digital geeks, can understand and apply in their daily lives. There were two main speakers, a large screen, a Powerpoint presentation and chairs for the audience. Although it was billed as a workshop, it was really more of an advice session/talk, with little opportunity to interact – one of the problems of running through a set of slides.
Pros
- Beginners welcome – had the most varied mix of people of all three events
- Darkened room for viewing slides, the acoustics weren't great though
- Practical advice on sending secure emails and messages, password managers, Tor browser
- Beginners friendly – idea of just 'change one thing'
- Friendly, open, inclusive vibe
- Resources posted on the Meetup site (Update: more resources, tips and follow-up from the session have now been posted to ORG B'ham)
Cons
- More political stance – which may put off some; would be good to know more about the trade-offs not just follow advice blindly
- Tried to pack too much in – people asking more in-depth questions but no time to cover
- Top-down talk – less engaging than a practical workshop
Summary
This was my first ORG session and the organisers obviously know their stuff, but it was a skim across the surface and felt like an intro session to a longer course. I think they could increase engagement with less content and more practical focus, and as the session started at 6.30pm, maybe see if they can get sponsorship for some refreshments as most people come directly from work.
The immersive option?
Data privacy is a hard sell, even though it's one of the biggest issues of our time with surveillance and data capture growing exponentially and often obfuscated and kept out of sight.
Most people know they should do 'something' but maybe think it's too techy, or a hassle, or like me, tell themselves that they'll get around to it one day and hope they don't get sprung in the meantime. In short, there are barriers for everyone to overcome.
This next event could be the answer… and I'm pleased to report that I've managed to get a spot helping out at The Glass Room London, which opens for three weeks at the end of October.
Curated by Tactical Tech and produced by Mozilla, The Glass Room, was attended by over 10,000 visitors in New York City last year.
It is ALL about the engagement, with people coming in off the street to an immersive, dystopian tech store that exposes the state of their data privacy. Data Detox Kits will be handed out. And there will be interactive exhibits.
It looks really really good, and will be blogged.
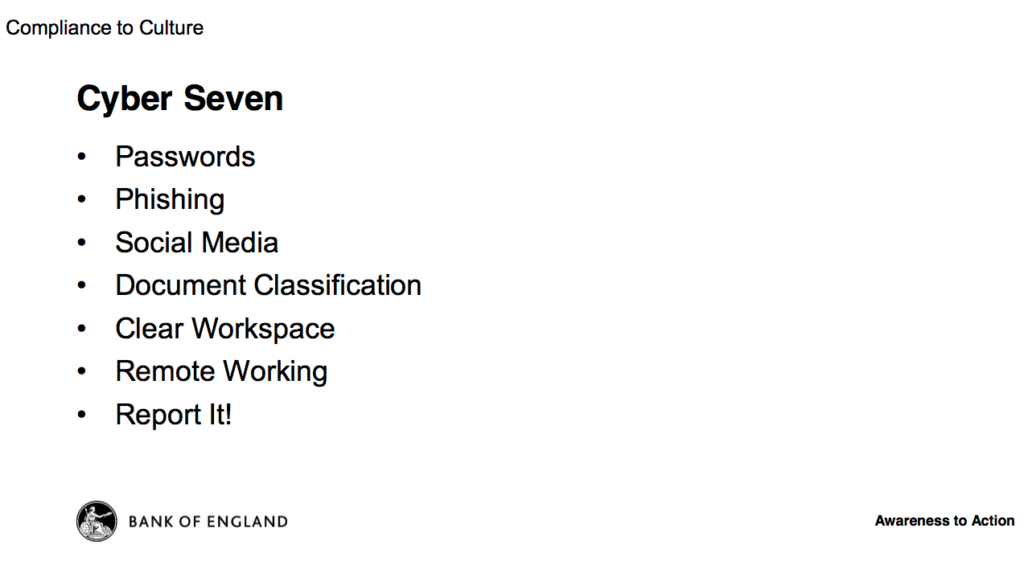
 A one-day event held yesterday held at Innovation Birmingham on the Aston Uni campus to help businesses get to grips with cybersecurity. It was organised by Metsi Technologies, and supported by the National Police Chiefs' Council and Regional Organised Crime Unit (ROCU) in the West Midlands. The Twitter account and hashtag was @cybersec_uk but the backchannel was pretty quiet. Here are my notes.
A one-day event held yesterday held at Innovation Birmingham on the Aston Uni campus to help businesses get to grips with cybersecurity. It was organised by Metsi Technologies, and supported by the National Police Chiefs' Council and Regional Organised Crime Unit (ROCU) in the West Midlands. The Twitter account and hashtag was @cybersec_uk but the backchannel was pretty quiet. Here are my notes.
 * and boob
* and boob



