The next round (Round 6) of the Mozilla Open Leaders programme is now open to applicants. You can find out more about it and how to apply here. But if you want a more personal read, here's my experience of the ups and downs for the record…
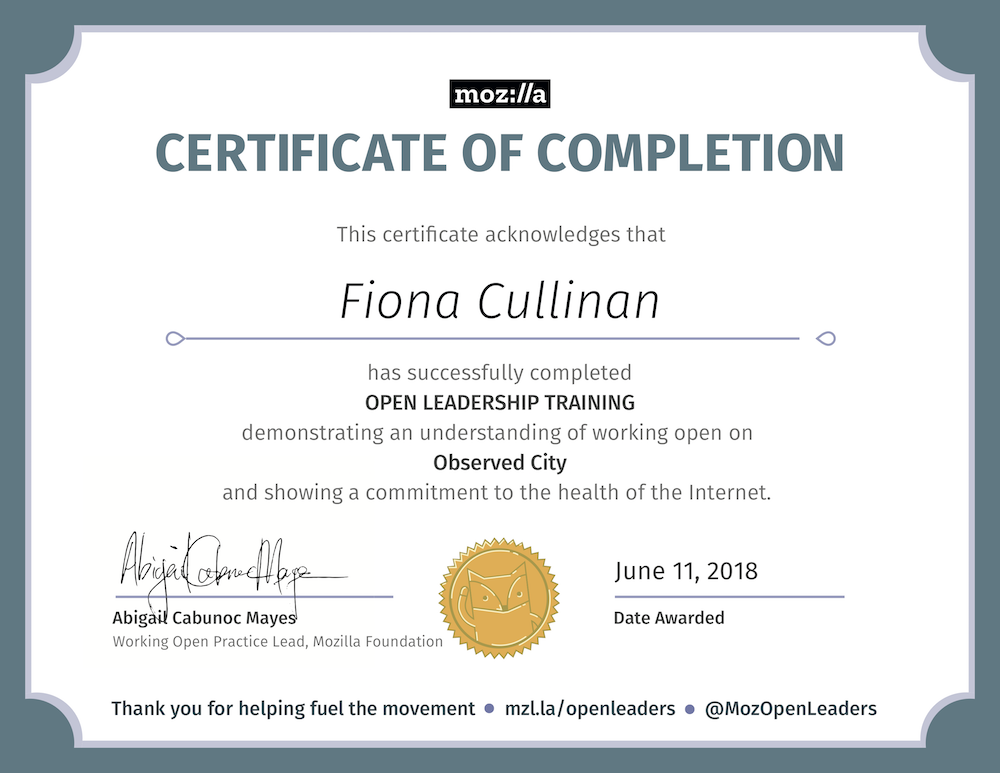
First off, I heartily recommend it. I've recently completed what I call MOLP, launched my project (click the logo below to join my data privacy email) and received my certificate of achievement. It's given me skills in project launch and management, working open, Github, online and IRL communities, and mentoring.
Given my project idea, I'm also happy to hear that the next round will feature a 'Data and You' theme. So, if you’re creating tools or raising awareness about personal data, you should apply. You have a very good chance on being accepted.
I have to admit, I wasn't really sure what I'd got myself into before I started. I just knew I wanted to get my idea off the ground. So what was the MOLP experience like?
You’re in! Now what?
After the elation of having your project idea accepted by Mozilla Open Leaders Project comes the realisation that you have to follow through. Now comes the work: 12-14 weeks of commitment. That's always a tough moment. Ideas are easy.
I can’t start without a name…
Some names come quickly, some take forever, some are a compromise that sticks. Someone telling me ‘you can always change it later’ was very freeing. In the end the lack of a name was holding up the project and there came a point when it was all I could think or even dream about. Each week I promised my mentor I'd have a name. It was very frustrating not to click with anything but it also felt important to get it right. Ultimately, my project name (Observed.City) arrived about three weeks in during some date night banter. It was unexpected and perfect.
The long and winding roadmap
The name of the project wasn't actually holding anything up. I was. Procrastination is a given so at least try to procrastinate in useful ways. I read a book on data privacy. I went to some events. I started a data reading group. It’s amazing what you can achieve when you’re avoiding work.
Slay your demons
Start at the beginning – or the end – but just start. Listing your tasks and goals is useful but these can always change. Mine were too rigid: two weeks on finding contacts and doing research, two weeks on creating content, two weeks on infrastructure and set up, leaving two weeks to launch. No no no! This didn’t work. What worked was addressing my demons, ie, too much thinking and not enough doing.
So I turned everything on its head and put out the first issue of my newsletter within a week – for better or worse. I realised that it only needed to be basic because I didn't actually have any subscribers. I wasn’t launching a perfect product, I was launching a minimal viable product. The pretty pictures and structure and subscribers could come later, once I figured out what I was doing.
Under pressure
Fear of failure can stifle a project but just stick with it and something will happen. A few MOLP projects drop out because their scope is too big for a 12-week programme or people underestimate the time it will take – if it's too much, reduce the scale of it or shape it so it fits your time and resources.
One thing I realised from getting my minimal viable product out in half the time was that it then gave me the space to focus on learning how to work openly, improving my Github and being available for the Q&As and project demos.
The pressure also came off when someone said to me: “No one cares as much about this as you.” So very true!
Create serendipitous ripples
Early on in the programme, everything is in your head and there’s a lot of work in learning how to articulate your project and your mission to others. By the end, though, you’ll be so confident about your one-sentence elevator pitch, you won’t even have to think about it.
Just by talking about your project, you create ripples: your own and then those of the people you talk to. Be direct in what you want, tell lots of people, ask for help and connections, offer to help, let serendipity occur…
There are many mentors
Having a mentor was a new thing. I thought, what can I learn from a radio astronomer? But it’s not about learning, it’s about being mentored: having someone to be answerable to, to encourage and support you, to give feedback, someone to check in with each week and talk over any issues. You’ll always be the expert on your project but your Mozilla mentor is there to help keep things on track and get your project set up for open working.
In fact, there are many available mentors when you’re mid-project. There are others in your Mozilla cohort – an academic in Addis Ababa and a New York technologist helped me quite directly on my Readme file and other Github pages, for example. I got feedback from Birmingham Open Rights Group on my approach. Even my family were mentors because calls to action such as ‘Just get on with it because I’m sick of hearing about it’ are actually incredibly valuable in helping you get on with the bloody thing.
Just nod and say yes
I was pushed out of my comfort zone a few times, for example, when presenting an online demo of my project. This was optional and so I was very tempted to ditch out and just watch others. My mentor sent me a long and encouraging email telling me exactly what was involved and said we could rehearse the tech side if I tuned in early. She added that if I could face it it would be a useful learning experience that would make me feel so much more confident after.
She was 100% right and, despite getting quite anxious when public speaking, I’m proud to say that I’ve now done two webcasts talking to a potential global audience.
It's over!
The newsletter is out there, it’s set up on Github for collaborators to join as and when, and I fully enjoyed and will miss meeting and talking with others from around the world as we all went through our projects together. I won’t lie, I was also happy to get my Tuesday cohort time back.
I feel a sense of achievement and it was much more enjoyable to go through a project launch as part of a wider group. Would I have done this on my own anyway? Maybe, but it wouldn’t have had a deadline and could easily have lapsed. And I wouldn't have had a clue how to set it up for inclusivity and collaboration. And the positive vibes of the Mozilla community were great for encouragement during the down times.
I’m much more comfortable with working open now so the Mozilla open learning framework has opened up the options for collaboration as well as how to structure future projects. I also understand a bit more about mentoring and how to address bias and diversity issues. So it's all good.
A new hope…
This is a journey that started at Mozfest last year, which was an eye-opening event in many ways, particularly in how we can help each other and share knowledge with the aim of a healthier internet and inclusive society.
It’s an unusually positive environment, and one that I would recommend on to anyone thinking about attending Mozfest or applying to be a Mozilla Open Leader or who wants some positive feedback for a change.
So that's it. The link to apply for the next round, which starts in September 2018 is here. Applications open mid-June.
For more info, I've blogged a bit more about MOLP and my project here.
Thanks for reading.
Hire/commission me: fiona [at] fionacullinan.com




 The Glass Room
The Glass Room What do you think about the current state of privacy online?
What do you think about the current state of privacy online? THERE WERE THREE themed areas to explore inside The Glass Room, with three further spaces to go deeper and find out more:
THERE WERE THREE themed areas to explore inside The Glass Room, with three further spaces to go deeper and find out more: THERE ARE THREE LESSONS I've taken away from my experience in The Glass Room to apply to any future sessions I might hold on these topics:
THERE ARE THREE LESSONS I've taken away from my experience in The Glass Room to apply to any future sessions I might hold on these topics: IT'S BEEN A MONTH SINCE The Glass Room and I'm proud of stepping up as an Ingenius and of overcoming my own fears and 'imposter syndrome'.
IT'S BEEN A MONTH SINCE The Glass Room and I'm proud of stepping up as an Ingenius and of overcoming my own fears and 'imposter syndrome'.
 Organised by:
Organised by:
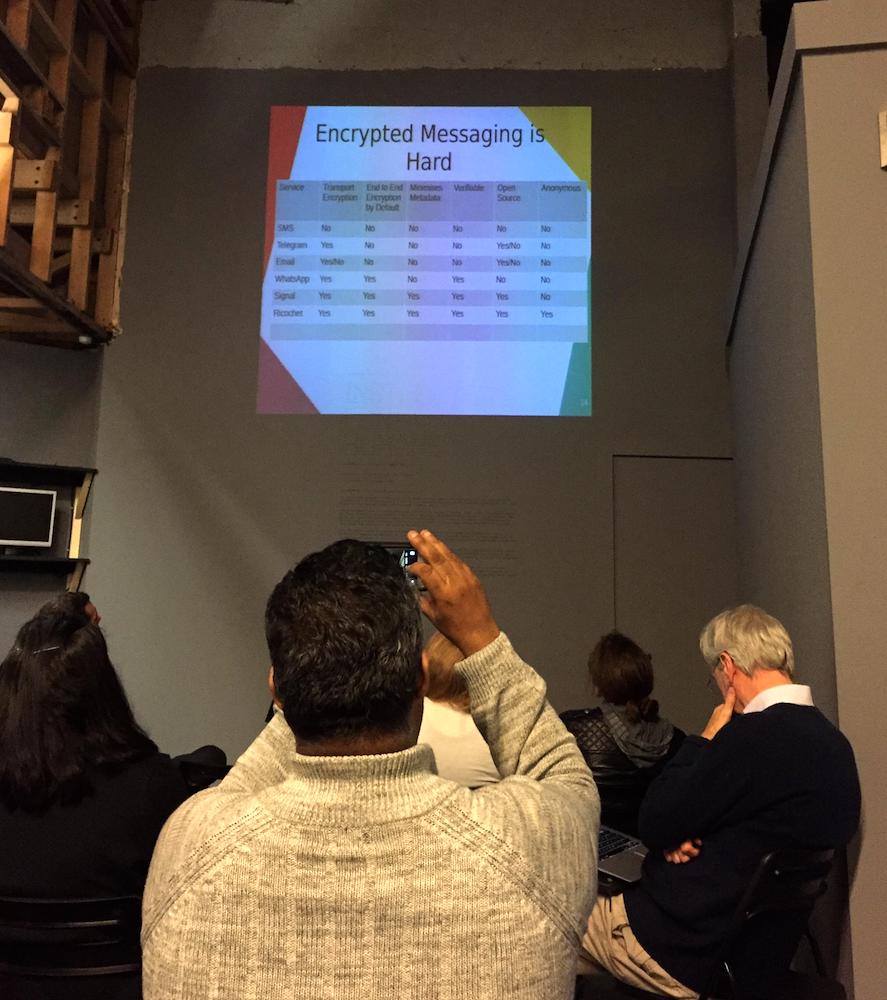
 A one-day event held yesterday held at Innovation Birmingham on the Aston Uni campus to help businesses get to grips with cybersecurity. It was organised by Metsi Technologies, and supported by the National Police Chiefs' Council and Regional Organised Crime Unit (ROCU) in the West Midlands. The Twitter account and hashtag was @cybersec_uk but the backchannel was pretty quiet. Here are my notes.
A one-day event held yesterday held at Innovation Birmingham on the Aston Uni campus to help businesses get to grips with cybersecurity. It was organised by Metsi Technologies, and supported by the National Police Chiefs' Council and Regional Organised Crime Unit (ROCU) in the West Midlands. The Twitter account and hashtag was @cybersec_uk but the backchannel was pretty quiet. Here are my notes.
 * and boob
* and boob